skip to main |
skip to sidebar

Infrastructures“We have built airports of international standard, upgraded domestic airports,Built seaports and the Roll-on/Roll-off System. I ask Congress for a PhilippineTransport Security Law..”Opinions:This would give easier transportations in every citizen in the country. The implemented project of President Arroyo was indeed contribute a sudden change in transporting products and even transporting our own self. The built international airports standard boost our confident to travel without any hesitations.
Roll-on/roll-off (RORO or ro-ro) ships are vessels designed to carry wheeled cargo such as automobiles, trucks, semi-trailer trucks, trailers or railroad cars that are driven on and off the ship on their own wheels. This is in contrast to lo-lo (lift on-lift off) vessels which use a crane to load and unload cargo. While the characteristics of seagoing RORO car ferries have inherent risks, there are benefits to its seaworthiness.
Banking System“To that end, we improved our banking system to complement its inherentConservatism. The Bangko Sentral has been prudent. Thank you, GovernorTetangco, being so effective. The BSP will be even more effectiveIf Congress will amend its Charter..”Opinions:In dealing with improving the bank system in the Philippines, we guarantee that it is more accurate and appropriate to use by. This would help million of Filipinos in complementing their inherent conservatism. Through improving the system of many companies here in the country, we are to take a big step towards global competition in the field of Information Technology. This would not help us feel better but as well us to be more confident about the saving of money of the country.
They were more efficient in certain banking aspects such as money transfers and current accounts, and borrowing loans and opening saving deposits. Banks adopt several means of acquiring assets or financing projects and these can be categorized in three areas: investment, trade and lending.Automated Electronic System“As the seeds of fundamental political reform are planted, let us address thehighest exercise of democracy -- voting! In 2001, I said we would finance fullyautomated elections. We got it, thanks to Congress..”Opinions:Well, basically automated elections are more convenient compare to manually done. They get a tally immediately, rather than having to count votes by hand. Philippine election officials can learn how to run automated elections properly. Primarily by designing election machines that make sense to the average Filipino voter, and relying on the results of sustained testing for any necessary revisions to the system. Automated voting (sometimes referred to as electronic or e-voting) technologies are increasingly used in elections across the world, particularly because they are often seen as symbolic of a country’s level of modernization.
The possibilities for rapid aggregation and analysis of results, as well as potentially greater accuracy, have all added to the attractiveness of computer-based voting equipment. There is little doubt that the ability to quickly publish results can be of particular advantage in conflict and post-conflict scenarios, where a prolonged period of counting can heighten tensions and reduce confidence in the final results. The potential to remove some traditional elements of unintentional voter error or intentional fraud can also contribute to greater confidenceSources:
http://en.wikipedia.org/wiki/RORO#Benefits
http://rtvm.gov.ph/attachments/1506_SONA%202009%20(As%20Delivered%20Tagalog-English%20version).pdf

It is my understanding that in the past 200 years, technology has advanced at an astonishing rate. Man’s advances in modern science have led to several cures for once common fatal diseases. I believe fundamentally, as humans, we have a desire to live eternally. In part, technology exists for that reason. Also, technology exists to “better our lives”. Just how much “better” our lives have become over the centuries could be argued? I see two sides to this issue. One train of thought says that technology has brought us leisure, comfort and knowledge. Another train of thought proclaims that we have become slaves to our jobs and the dependence of technology. Cogs in a great combine.
The technology which surrounds almost everyone in the modern society, affects both work and leisure activities. Technology contains information that many would rather it did not have. It influences minds in good and bad ways, and it allows people to share information which they would otherwise not be able to attain. Even if a person does not own a computer or have credit cards, there is information on a computer somewhere about everyone. The technology which is just now beginning to be manipulated and harnessed is affecting the minds of small children and adolescents in ways that could be harmful. It is affecting our immediate future. It also gives another form of communication and exchange of information which was not available before, information that is both good and bad. Technology is one of the principal driving forces of the future; it is transforming our lives and shaping our future at rates unprecedented in history, with profound implications which we can't even begin to see or understand.
Many different elements affect how satisfied we are with our lives. The impact of technology on these elements can change how safe, healthy and happy people feel. Throughout history, people have looked for better ways to meet their needs and to satisfy their expectations. Technology has improved the way people feed, clothe and shelter themselves. Technology has also changed other aspects of everyday life, such as health care, education, job satisfaction, and leisure time activities. People have used technology since them first chipped stone blades to improve their hunting. Yet some people call the current age the Technological Age because of society's dependence on technology. For the first time in human history, almost all the goods and services people use depend on technology.
The products of technology are available to almost everyone in society. The economy of a country influences how the people of the county live. Technology is often considered the key to a nation's economic growth. Most economists would say that it is one of the factors in economic growth, but they would probably disagree about its importance. Many economists think that if technology sparks growth in one sector of the economy in the form of increased productivity, growth will also occur in other sectors of the economy. Jobs may be lost in one industry, such as agriculture but new jobs may emerge in other sectors of the economy. There may be more jobs or, in some case, completely new kinds of jobs. Technology may also be used to solve urgent problems.
Our growing population is using up infinite supplies of natural resources. Innovations in technology can allow for more efficient use of limited or scarce resources. More products might be made from the same amount of raw material using new techniques. Technology can increase productivity to help countries compete with other countries in selling goods and services. Some say that without technological improvements, the economy would grow slowly or not at all.
What is Corporation?
Corporations exist as a product of corporate law, and their rules balance the interests of the management who operate the corporation; creditors who loan it goods, services or money; shareholders that invest their capital and the employees who contribute their labor. People work together in corporations to produce value and generate income. In modern times, corporations have become an increasingly dominant part of economic life. People rely on corporations for employment, for their goods and services, for the value of the pensions, for economic growth and social development.
The defining feature of a corporation is its legal independence from the people who create it. If a corporation fails, shareholders normally only stand to lose their investment and employees will lose their jobs, but neither will be further liable for debts that remain owing to the corporation's creditors unless they have separately varied this, e.g. with personal guarantees. This rule is called limited liability, and it is why the names of corporations in the UK end with "Ltd.".
The Great Transformation
Sparked by new technologies, particularly the Internet, the corporation is undergoing a radical transformation that is nothing less than a new Industrial Revolution. This time around, the revolution is reaching every corner of the globe and in the process, rewriting the rules laid down by Sloan, Henry Ford, and other Industrial Age giants. The 21st century corporation that emerges will in many ways be the polar opposite of the organizations they helped shape.
The New Leadership
In recent years, top corporate executives have reaped a pay bonanza without precedent in the long and sweaty history of working for a living. Is today's boss overpaid? Probably, but to whom much has been given, even more will be expected. The job of leading a company has never been more demanding, and it will only get tougher in the 21st century.
The Enduring Corporation
Government also expects much more from the corporation than it did a generation ago. For some time now, corporations have been America's largest distributors of health care and private pension benefits. In recent years government also has increasingly looked to business to regulate employee behavior in the workplace in new ways, giving rise to the so-called nanny corporation.
The Ecosystem
The corporate ecosystem of the 21st century will be characterized by a blurring of once-distinct boundaries: between public and private, foreign and domestic, insider and outsider, friend and foe. The effect will be liberating in many ways. Corporations will be freer to pursue opportunity wherever in the world they find it, and to exploit it according to the requirements of circumstance, not the blind dictates of tradition. Outsourcing will become ever more prevalent, transforming many corporations into superefficient, virtual facsimiles of their old selves. But success will not come easy in this brave new world.
Designs for the Future
Few institutions embody their era as strikingly as the corporation. In form and function, it reflects the defining technologies and social organization of its time. This is as true of the physical manifestation as internal configuration, which is why corporations have captured the imagination of so many visionaries, especially architects.
Sources:
http://www.businessweek.com/2000/00_35/b3696001.htmhttp://en.wikipedia.org/wiki/21st_Century
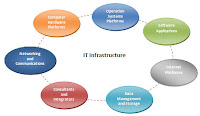 A cohesive and robust IT infrastructure is of paramount importance for the development of any company. A successful IT department must be able to meet increasing business driven demands, whilst preparing for changing business dynamics in the future.
A cohesive and robust IT infrastructure is of paramount importance for the development of any company. A successful IT department must be able to meet increasing business driven demands, whilst preparing for changing business dynamics in the future.
If I were hired by the university president as an IT consultant, I would you suggest to use or develop such Infrastructures in University. This is to improve not only the system of the University but as well as transactions, internet access and even operations made by the staff.
We define information technology (IT) to include not only computer technology (hardware and software) for processing and storing information, but also communications technology for transmitting information. Advances in computer and communications technologies have enabled firms to pursue IT investments. This will help them to gain maximum advantage from their knowledge assets-to leverage the knowledge of individual employees to the benefit of other employees and the organization as a whole. Businesses have strived to achieve a competitive advantage in the past by competing in one of two ways: 1. By Cost- by being a low-cost producer of a good and service 2. By Differentiation of a product or service- by competing on customer perceptions of product quality and customer support services.
You know, there is not all that much I would actually change about this university. Sure we could use some better facilities and the more diversity the better, but those changes have to take place over time, sometimes a long time. For now I am content with the prospect of throwing out ideas used by other universities to either increase student recruitment or enhance the image surrounding our college, that has without doubt been tarnished in past years.
Infrastructure can be defined as the basic physical and organizational structures needed for the operation of a society or enterprise, or the services and facilities necessary for an economy to function. The term typically refers to the technical structures that support a society, such as roads, water supply, sewers, power grids, telecommunications, and so forth. An underlying base or foundation especially for an organization or system. The basic facilities, services, and installations needed for the functioning of a community or society, such as transportation and communications systems, water and power lines, and public institutions including schools, post offices, and prisons. It s the set of interconnected structural elements that provide the framework for supporting the entire structure.
In other applications, the term infrastructure may refer to information technology, informal and formal channels of communication, software development tools, political and social networks, or beliefs held by members of particular groups. Still underlying these more conceptual uses is the idea that infrastructure provides organizing structure and support for the system or organization it serves, whether it is a city, a nation, a corporation, or a collection of people with common interests.
In the present world, which is dynamic and knowledge based, universities have a much wider role to play in creating, preserving, organizing, transmitting and applying knowledge. Modern educational technologies developed from information technology will certainly change in terms of access, interaction, curriculum and instruction etc. The physical locations and facilities will be less important in defining a college or a university due to the easy on-line access of the educational resources of a higher educational institution to the urban as well as rural public. This will provide opportunities to our high school graduated youths from rural areas as well as urban youths to access higher education without a need to forgo their working and earning opportunities to physically attend a college or a university. So universities need to adopt modern education technologies to provide increase access to knowledge resources.
Online technologies are going to make traditional class room teaching less important in many subjects except where it is absolutely necessary. Therefore interaction between teachers and students will have to play a vital role in imparting higher quality education. This means that more frequent and effective internal mechanism of interaction between university faculty and students need to be developed. This, in turn, causes an external relationship between universities and non-university communities. Such external relationship will necessitate universities to respond quickly to the changes in the outside world. Therefore a mechanism to increase both the internal and external interaction efficiencies has to be developed.
The curriculum and instruction are going to be changed greatly. Because the new technologies make the learning and teaching easier, the contents of some courses will be expanded, a considerable number of new courses will be generated, interdisciplinary courses and studies will be more possible. Students and faculties will contribute together to the development of curriculum.
Modern higher education technologies will also change present instructional methods to a more effective one. The faculties will have to adopt an instructional method best suited to the class of students whom they target or to develop new methods best suited for them based on their feedback. Video conferencing techniques, simulators and on-line access to many practical training kits will revolutionize instructional methods. Information Technology infrastructure in the campus provide quality higher education to students and to provide proper academic and research environment to support University’s endeavor for excellence.
More importantly, these technologies will provide the education and knowledge for these people to become prosperous nations that can fend for themselves and provide for their people. Transfers of technology from the developed world to the developing world will improve the standard of living, increase efficiency in production and become a base for economic growth, without this transfer these countries will fall further into poverty and economic ruin, with little hope for survival. For most people of the developed world, the developing world is not something they concern themselves with; they do not see it everyday and therefore it does not exist. This could not be farther from the truth. The developing world is in need of help but the developed world constantly turns a blind eye. Our current love affair with technology may provide the answer for underdeveloped nations problems. The standard of living is so low in these countries that our everyday conveniences are a struggle for the entire population to obtain. If the developed nations could meet these base needs, these countries may be able to overcome their current problems. The first issue that must be dealt with is the unsatisfactory health care and medical technology.
Most IT organizations still install and maintain computers the same way the automotive industry built cars in the early 1900's: An individual craftsman manually manipulates a machine into being, and manually maintains it afterward. This is expensive. The automotive industry discovered first mass production, then mass customization using standard tooling.
The standards and practices described here are the standarized tooling needed for mass customization within IT. This tooling enables:
• Scalable, flexible, and rapid deployments and changes
• Cost effective, timely return on IT investment
• Low labor headcount
• Secure, trustworthy computing environments
• Reliable enterprise infrastructures
This are the 5 services which Information Technology Infrastructures can give to the University:
1. Service Strategy
As the center and origin point of the ITIL Service Lifecycle, the Service Strategy volume provides guidance on clarification and prioritization of service provider investments in services. More generally, Service Strategy focuses on helping IT organizations improve and develop over the long term. In both cases, Service Strategy relies largely upon a market-driven approach. Key topics covered include service value definition, business case development, service assets, market analysis, and service provider types. Processes covered include service portfolio management, demand management, and IT financial management.
2. Service Design
The ITIL Service Design volume provides good practice guidance on the design of IT services, processes, and other aspects of the service management effort. Significantly, design within ITIL is understood to encompass all elements relevant to technology service delivery, rather than focusing solely on design of the technology itself. As such, Service Design addresses how a planned service solution interacts with the larger business and technical environments, service management systems required to support the service, processes which interacts with the service, technology, and architecture required to support the service, and the supply chain required to support the planned service. Within ITIL, design work for an IT service is aggregated into a single Service Design Package (SDP). Service Design Packages, along with other information about services, are managed within the service catalog. Processes covered in this volume include service level management, availability management, capacity management, IT service continuity management, information security management, supplier management, and service catalog management.
3. Service Transition
Service transition relates to the delivery of services required by the business into live/operational use, and often encompasses the "project" side of IT rather than "BAU" (Business As Usual). This area also covers topics such as managing changes to the "BAU" environment. Topics include Service Asset and Configuration Management, Transition Planning and Support, Release and deployment management, Change Management, Knowledge Management, as well as the key roles of staff engaging in Service Transition.
4. Service Operation
Best practice for achieving the delivery of agreed levels of services both to end-users and the customers (where "customers" refer to those individuals who pay for the service and negotiate the SLAs). Service Operations is the part of the lifecycle where the services and value is actually directly delivered. Also the monitoring of problems and balance between service reliability and cost etc are considered. Topics include balancing conflicting goals (e.g. reliability vs cost etc), Event management, incident management, problem management, request fulfillment, access management, and service desk. The functions include technical management, application management, operations management and Service Desk as well as, responsibilities for staff engaging in Service Operation.
5. Continual Service Improvement (CSI)
Aligning and realigning IT services to changing business needs (because standstill implies decline).
The goal of Continual Service Improvement is to align and realign IT Services to changing business needs by identifying and implementing improvements to the IT services that support the Business Processes. The perspective of CSI on improvement is the business perspective of service quality, even though CSI aims to improve process effectiveness, efficiency and cost effectiveness of the IT processes through the whole lifecycle. To manage improvement, CSI should clearly define what should be controlled and measured.
CSI needs to be treated just like any other service practice. There needs to be upfront planning, training and awareness, ongoing scheduling, roles created, ownership assigned, and activities identified to be successful. CSI must be planned and scheduled as process with defined activities, inputs, outputs, roles and reporting.
Infrastructure Management
ICT Infrastructure Management processes recommend best practice for requirements analysis, planning, design, deployment and ongoing operations management and technical support of an ICT Infrastructure. ("ICT" is an acronym for "Information and Communication Technology".)
The Infrastructure Management processes describe those processes within ITIL that directly relate to the ICT equipment and software that is involved in providing ICT services to customers.
• ICT Design and Planning • ICT Deployment
• ICT Operations
• ICT Technical Support
These disciplines are less well understood than those of Service Management and therefore often some of their content is believed to be covered 'by implication' in Service Management disciplines.
In information technology and on the Internet, infrastructure is the physical hardware used to interconnect computers and users. Infrastructure includes the transmission media, including telephone lines, cable television lines, and satellites and antennas, and also the routers, aggregators, repeaters, and other devices that control transmission paths. Infrastructure also includes the software used to send, receive, and manage the signals that are transmitted.
In some usages, infrastructure refers to interconnecting hardware and software and not to computers and other devices that are interconnected. However, to some information technology users, infrastructure is viewed as everything that supports the flow and processing of information.
Infrastructure companies play a significant part in evolving the Internet, both in terms of where the interconnections are placed and made accessible and in terms of how much information can be carried how quickly.
Service Support
The Service Support discipline is focused on the User of the ICT services and is primarily concerned with ensuring that they have access to the appropriate services to support the business functions.
To a business, customers and users are the entry point to the process model. They get involved in service support by:
• Asking for changes
• Needing communication, updates
• Having difficulties, queries.
• Real process delivery
The service desk is the single contact point for customer’s problems. If there is a direct solution, it tries to resolve the problem. If not, it creates an incident.
Service Desk / Service Request Management
Tasks include handling incidents and requests, and providing an interface for other ITSM processes.
• Single Point of Contact (SPOC) and not necessarily the First Point of Contact (FPOC)
• There is a single point of entry and exit
• Easier for Customers
• Data Integrity
• Communication channel is streamlined
The primary functions of the Service Desk are:
• Incident Control: life cycle management of all Service Requests
• Communication: keeping the customer informed of progress and advising on workarounds
The Service Desk function is known under various names .
• Call Center: main emphasis on professionally handling large call volumes of telephone-based transactions
• Help Desk: manage, co-ordinate and resolve incidents as quickly as possible
• Service Desk: not only handles incidents, problems and questions but also provides an interface for other activities such as change requests, maintenance contracts, software licenses, service level management, configuration management, availability management, Financial Management and IT Services Continuity Management
The three types of structure that can be considered are:
• Local Service Desk: to meet local business needs - is practical only until multiple locations requiring support services are involved
• Central Service Desk: for organizations having multiple locations - reduces operational costs and improves usage of available resources
• Virtual Service Desk: for organizations having multi-country locations - can be situated and accessed from anywhere in the world due to advances in network performance and telecommunications, reducing operational costs and improving usage of available resources
Incident Management
The goal of Incident Management is to restore normal service operation as quickly as possible and minimize the adverse effect on business operations, thus ensuring that the best possible levels of service quality and availability are maintained. 'Normal service operation' is defined here as service operation within Service Level Agreement (SLA) limits.
Problem Management
The goal of 'Problem Management' is to resolve the root cause of incidents and thus to minimize the adverse impact of incidents and problems on business that are caused by errors within the IT infrastructure, and to prevent recurrence of incidents related to these errors. A `problem' is an unknown underlying cause of one or more incidents, and a `known error' is a problem that is successfully diagnosed and for which either a work-around or a permanent resolution has been identified. The CCTA defines problems and known errors as follows:
The problem management process is intended to reduce the number and severity of incidents and problems on the business, and report it in documentation to be available for the first-line and second line of the help desk. The proactive process identifies and resolves problems before incidents occur. These activities are:
• Trend analysis;
• Targeting support action;
• Providing information to the organization.
The Error Control Process is an iterative process to diagnose known errors until they are eliminated by the successful implementation of a change under the control of the Change Management process.
The Problem Control Process aims to handle problems in an efficient way. Problem control identifies the root cause of incidents and reports it to the service desk. Other activities are:
• Problem identification and recording;
• Problem classification;
• Problem investigation and diagnosis.
Change Management
The goal of Change Management is to ensure that standardized methods and procedures are used for efficient handling of all changes,
The main aims of Change Management are:
• Minimal disruption of services
• Reduction in back-out activities
• Economic utilization of resources involved in the change
Change Management Terminology
• Change: the addition, modification or removal of CIs
• Request for Change (RFC): form used to record details of a request for a change and is sent as an input to Change Management by the Change Requestor
• Forward Schedule of Changes (FSC): schedule that contains details of all forthcoming Changes
Release Management
Release Management is used for platform-independent and automated distribution of software and hardware, including license controls across the entire IT infrastructure. Proper software and hardware control ensures the availability of licensed, tested, and version-certified software and hardware, which functions as intended when introduced into existing infrastructure. Quality control during the development and implementation of new hardware and software is also the responsibility of Release Management. This guarantees that all software meets the demands of the business processes. The goals of release management are:
• Plan the rollout of software
• Design and implement procedures for the distribution and installation of changes to IT systems
• Effectively communicate and manage expectations of the customer during the planning and rollout of new releases
• Control the distribution and installation of changes to IT systems
The focus of release management is the protection of the live environment and its services through the use of formal procedures and checks.
Release Categories
A Release consists of the new or changed software and/or hardware required to implement approved changes
Releases are categorized as:
• Major software releases and hardware upgrades, normally containing large amounts of new functionality, some of which may make intervening fixes to problems redundant. A major upgrade or release usually supersedes all preceding minor upgrades, releases and emergency fixes.
• Minor software releases and hardware upgrades, normally containing small enhancements and fixes, some of which may have already been issued as emergency fixes. A minor upgrade or release usually supersedes all preceding emergency fixes.
• Emergency software and hardware fixes, normally containing the corrections to a small number of known problems.
Releases can be divided based on the release unit into:
• Delta Release: is a release of only that part of the software which has been changed. For example, security patches.
• Full Release: means the entire software program is deployed—for example, a new version of an existing application.
• Packaged Release: is a combination of many changes—for example, an operating system image which also contains specific applications.
Sources:
http://en.wikipedia.org/wiki/Information_Technology_Infrastructure_Library#ICT_Infrastructure_Managementhttp://searchdatacenter.techtarget.com/sDefinition/0,,sid80_gci212346,00.html
The technology which surrounds almost everyone in the modern society, affects both work and leisure activities. Technology contains information that many would rather it did not have. It influences minds in good and bad ways, and it allows people to share information which they would otherwise not be able to attain. Even if a person does not own a computer or have credit cards, there is information on a computer somewhere about everyone. The technology which is just now beginning to be manipulated and harnessed is affecting the minds of small children and adolescents in ways that could be harmful. It is affecting our immediate future. It also gives another form of communication and exchange of information which was not available before, information that is both good and bad.
Technology is one of the principal driving forces of the future; it is transforming our lives and shaping our future at rates unprecedented in history, with profound implications which we can't even begin to see or understand. Many different elements affect how satisfied we are with our lives. The impact of technology on these elements can change how safe, healthy and happy people feel.
How to overcome Barriers to Information Technology/ Information System? Here are some examples states hot to overcome these barriers.
Overcoming barriers to information
Brian Martin, The University of Wollongong
What stops timely public access to information that people need and want to know? The answer is relatively easy: a range of barriers to information access, such as bureaucratic secrecy, defamation law and corporate pressure on the media. What is the best way to remove these barriers? The answer to this question is much harder.
An information strategy is an organised way of moving towards a desirable information future, taking into account the current reality, available resources, opponents and obstacles. There aren’t many people acting on the basis of explicit grand strategies, but there are quite a few making valuable contributions. The sum total of efforts in the same general direction can be thought of as a de facto strategy.
So let’s look at some de facto strategies in the information sphere, to see what can be learned. To begin, it’s useful to spell out some specific obstacles to information access. I focus on five particular ones (Martin, 1998).
• Government and corporate influences on mass media range from heavy-handed attempts to stop stories to the subtle self-censorship deriving from a fear of offending advertisers or sources. Typical things covered up include embarrassing policy failures and corporate malfeasance. Pressure is normally applied to editors and journalists behind the scenes; this pressure is seldom justified publicly.
• Defamation law is used to stop publication of critical material about individuals and organisations. For example, politicians and entrepreneurs may threaten to sue, and seeing the costs of actual suits scares potential targets, leading to excessive caution even when defamation suits are unlikely. The stated rationale for defamation is protection of reputation, but it is far more effective as a form of censorship. Strategic Lawsuits Against Public Participation (SLAPPs) most commonly use defamation law (Pring and Canan, 1996).
• Intellectual property is used to restrict access to cheap copies of information and to inhibit innovation building on proprietary materials. The cost of intellectual property reduces access to databases, scientific articles, photographs and music, while worries about legal action inhibit efforts to create improved or creatively modified versions of existing works. Intellectual property is supposed to promote innovation but often slows it by creating intellectual monopolies and by reducing the "intellectual commons"—the public domain—which is the foundation for inspiration and innovation.
• Bureaucratic controls, especially in government and corporate organisations, are used to prevent disclosure of inside information. Employees know an enormous amount about corruption and bad policy but are subject to serious reprisals if they speak out. The usual rationale for organisational secrecy is efficiency; routine leaks by senior bureaucrats reveal a double standard. The power of the bureaucratic hierarchy induces conformity in most employees.
• Misleading information is produced in vast quantities by advertisers, governments and other vested interests, overloading people and making it hard to recognise what is really important. The constant diet of biased and inadequate information leads to confusion and cynicism, while independent sources of information are relegated to the sidelines. Production of misleading information is justified as freedom of speech.
Lack of adequate financial support is top IT implementation barrier.
Financial pressures are a powerful limitation on capital investment in information technology. The top three IT implementation barriers cited by 2001 survey respondents are lack of adequate financial support for IT (21%), difficulty proving IT quantifiable benefits/ROI (15%), and vendors’ inability to effectively deliver product or service to respondents’ satisfaction (14%). Although it is still a top concern, difficulty in proving ROI has decreased in significance from 22% last year.
Accessing capital and demonstrating return-on-investment are not the only challenges. While recruiting and retaining high-quality IT staff was mentioned, staffing concerns dropped for the second year in a row; only 6% of respondents cited it as a barrier, compared to 15% in 2000, and 23% in 1999.
I believe that every company has its own Information System or Information Technology Barriers, same with the company I adopted, they also facing this rampant situation in processing high technologies. Here are some obstacles in Information Management which also encountered most of the company today.
Obstacles to information sharing and their management
1. What are the obstacles to information-sharing?
Human resource problems
• Insufficient skilled management in information-gathering and retrieving information
• Insufficient trained personnel at all levels
• Insufficient communication skills
Technical resource problems
• Need for modern information systems
• Difficulties in setting up information programme
• Problems in data processing
• Technical constraints to reproducing or copying documents
• Decoding statistics collected and the structure of statistical reporting
• Time factor in the collection and updating of information
• Need for qualitative aspects of information
Physical resource problems
• Need for publishing houses
• Need for documentation centres
Financial problems
• Need for funds for processing, printing and dissemination of information
Communication problems
• Production of incomprehensible information
• Insufficient understanding of the objectives, goals and aims of programmes
• Top-down approach
• Languages: media of communication
• Information-filtering
• Untargeted information
• Insufficient understanding among interest groups
Operational problems
• Need for co-ordination and networking among professionals and educational institutions
• Need for supportive policy to release information
• Insufficient access to information source
• Confidentiality
• Redundancy of information
• Nature of policy directives
• Need for identifying sources of information
• Centralization of activities
• Need for systematic documentation
Psychological and other problems
• Need for mutual trust between professionals and administrators
• Need for trust in information-sharing
• Need for of goodwill
• Competition between organizations
• Censorship
• War
2. How can these obstacles be effectively managed?
Human resource development
• Training
• Other capacity-building
Technical resource development
• Establish documentation centre (independent non-governmental institution for processing and disseminating information ?)
• Install modern information technology
• Create database
• Encourage small-scale publishing
Physical resource development
• Improve infrastructure
• Build documentation centre
Operational improvement
• Set clear policy guidelines on information dissemination
• Encourage government to have depository laws and enforce them
• Introduce information system
• Use mass media
• Follow a bottom-up approach
• Develop grassroots level inventory of information
• Create awareness of the value of information
• Identify user information needs
• Consult target groups
• Develop target-oriented and useable information
• Develop effective system of information management and dissemination; information should be simple, understandable and manageable
• Institute efficient and effective co-ordination and networking
• Encourage a free flow of information — horizontally and vertically
Common Barriers in Information Technology
• When information technology is designed so that it does not work with assistive technology, it creates barriers to people with disabilities.
• Software that requires the use of a mouse to perform commands is inaccessible to people with disabilities that cannot use a mouse.
• A copier that has controls outside of accessible reach ranges is inaccessible for some persons who use wheelchairs.
• A computer laboratory that is located in an inaccessible building cannot be accessed by people with disabilities.
• Some of the barriers listed above are primarily the responsibility of IT vendors, but educational entities should take these barriers into account in the procurement process.
•
Sources:
http://www.australianreview.net/digest/2002/04/martin.html
http://www.unesco.org/education/educprog/erd/english/wgesa/doc/ethiopia/appendice_2.htm



